Difference between revisions of "Trust Architecture"
| (21 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
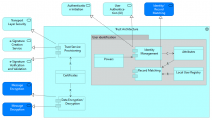
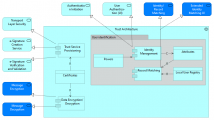
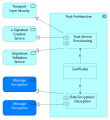
| + | The Trust Architecture application collaboration aggregates multiple co-operating application components realizing all needed services to implement the DE4A trust models. The identity management application component is used by the DC to initiate the authentication process and it implements functionality so the user can authenticate him/herself. Both DC and DP use the component to perform the identity matching based on attributes. The Trust Service provisioning component is also used by both DC and DP to provide functionality to handle the digital signing of messages. The data encryption/decryption component is again used by both DC and DP to support the encryption and decryption of messages. The Trust Architecture also provides functionality so that natural persons can represent other natural and legal persons. | ||
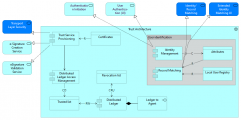
| − | + | For [[Verifiable Credentials Pattern|VC]] the collaboration between these components is similar. The interaction between the user identification components remains the same. In addition to creating, verifying and validating digital signatures, the Trust Provisioning Component now also needs to retrieve the DP certificates and communicates with the Distributed ledger access management component to store the certificates to the Trusted list stored/retrieved to/from the Distributed Ledger (instead of persistent storage in the Intermediation pattern). | |
| − | + | <gallery widths="400" perrow="4" caption="Graphic representations of the Trust Architecture application collaboration"> | |
| − | + | File:Trust Architecture (Inter).png|alt=Graphic representation of the Trust Architecture application collaboration in the Intermediation Pattern|[[Intermediation Pattern|IM]] | |
| − | <gallery widths="400" perrow=" | + | File:Trust Architecture (USI).png|alt=Graphic representation of the Trust Architecture application collaboration in the User Supported Intermediation Pattern|[[User-supported Intermediation Pattern|USI]] |
| − | File: | + | File:Trust_Architecture_VC.png|alt=Graphic representation of the Trust Architecture application collaboration in the Verifiable Credentials Pattern|[[Verifiable Credentials Pattern|VC]] |
| − | File: | + | File:Trust Architecture (S&N).png|alt=Graphic representation of the Trust Architecture application collaboration in the Subscription & Notification Pattern|[[Subscription and Notification Pattern|S&N]] and and [[Lookup Pattern|LKP]] |
| − | File: | ||
</gallery> | </gallery> | ||
| Line 16: | Line 16: | ||
! Application Component !! Description !! Pattern(s) | ! Application Component !! Description !! Pattern(s) | ||
|- | |- | ||
| − | | [[ | + | | [[Trust Service Provisioning]] |
| Implements the functionalities encapsulating the trust services functionalities. | | Implements the functionalities encapsulating the trust services functionalities. | ||
A ‘trust service’ means an electronic service which consists of these functionalities: | A ‘trust service’ means an electronic service which consists of these functionalities: | ||
| Line 25: | Line 25: | ||
iii) the preservation of electronic signatures, seals or certificates related to those services. | iii) the preservation of electronic signatures, seals or certificates related to those services. | ||
| − | | [[Intermediation Pattern|IM]], [[USI]], [[VC]] | + | | [[Intermediation Pattern|IM]], [[User-supported Intermediation Pattern|USI]], [[Verifiable Credentials Pattern|VC]], [[Subscription and Notification Pattern|S&N]], [[Lookup Pattern|LKP]] |
|- | |- | ||
| − | | [[ | + | | [[Identity Management]] |
| Implements the functionality of user authentication. | | Implements the functionality of user authentication. | ||
‘Electronic identification’ means the process of using person identification data in electronic form uniquely representing either a natural or legal person, or a natural person representing a legal person; | ‘Electronic identification’ means the process of using person identification data in electronic form uniquely representing either a natural or legal person, or a natural person representing a legal person; | ||
| − | ‘Authentication’ means an electronic process that enables the electronic identification of a natural or legal person, or the origin and integrity of | + | ‘Authentication’ means an electronic process that enables the electronic identification of a natural or legal person, or the origin and integrity of data in electronic form to be confirmed. |
| − | | [[Intermediation Pattern|IM]], [[USI]], [[VC]] | + | | [[Intermediation Pattern|IM]], [[User-supported Intermediation Pattern|USI]], [[Verifiable Credentials Pattern|VC,]] |
|- | |- | ||
| [[Record Matching]] | | [[Record Matching]] | ||
| Application component that provides identity matching based on attributes. Provided attributes are matched against attributes in some local registry. | | Application component that provides identity matching based on attributes. Provided attributes are matched against attributes in some local registry. | ||
| − | | [[Intermediation Pattern|IM]], [[USI]], [[VC]] | + | | [[Intermediation Pattern|IM]], [[User-supported Intermediation Pattern|USI]], [[Verifiable Credentials Pattern|VC]] |
|- | |- | ||
| [[Data Encryption/Decryption]] | | [[Data Encryption/Decryption]] | ||
| Application component providing encryption and decryption functionality (symmetrical, asymmetrical or a combination thereof). | | Application component providing encryption and decryption functionality (symmetrical, asymmetrical or a combination thereof). | ||
| − | | [[Intermediation Pattern|IM]], [[ | + | | [[Intermediation Pattern|IM]], [[User-supported Intermediation Pattern|USI]], [[Subscription and Notification Pattern|S&N,]] [[Lookup Pattern|LKP]] |
| − | |||
| − | | | ||
| − | |||
| − | |||
|- | |- | ||
| [[Distributed Ledger]] | | [[Distributed Ledger]] | ||
| Application component that handles connections and operations related to the distributed ledger. | | Application component that handles connections and operations related to the distributed ledger. | ||
| − | | [[VC]] | + | | [[Verifiable Credentials Pattern|VC]] |
|- | |- | ||
| [[Distributed Ledger Access Management]] | | [[Distributed Ledger Access Management]] | ||
| Application component that manages the access management related to Write/Read access into distributed ledger storage. | | Application component that manages the access management related to Write/Read access into distributed ledger storage. | ||
| − | | [[VC]] | + | | [[Verifiable Credentials Pattern|VC]] |
|- | |- | ||
|[[Ledger to Agent]] | |[[Ledger to Agent]] | ||
| − | | | + | |Interface that will connect to the Distributed Ledger (i.e., EBSI) in order to use e.g., the DID registry, Trusted Issuer Registry (TIR), Revocation list, etc. |
| − | |[[VC]] | + | |[[Verifiable Credentials Pattern|VC]] |
|- | |- | ||
|} | |} | ||
Latest revision as of 15:52, 23 June 2021
The Trust Architecture application collaboration aggregates multiple co-operating application components realizing all needed services to implement the DE4A trust models. The identity management application component is used by the DC to initiate the authentication process and it implements functionality so the user can authenticate him/herself. Both DC and DP use the component to perform the identity matching based on attributes. The Trust Service provisioning component is also used by both DC and DP to provide functionality to handle the digital signing of messages. The data encryption/decryption component is again used by both DC and DP to support the encryption and decryption of messages. The Trust Architecture also provides functionality so that natural persons can represent other natural and legal persons.
For VC the collaboration between these components is similar. The interaction between the user identification components remains the same. In addition to creating, verifying and validating digital signatures, the Trust Provisioning Component now also needs to retrieve the DP certificates and communicates with the Distributed ledger access management component to store the certificates to the Trusted list stored/retrieved to/from the Distributed Ledger (instead of persistent storage in the Intermediation pattern).
- Graphic representations of the Trust Architecture application collaboration
| Application Component | Description | Pattern(s) |
|---|---|---|
| Trust Service Provisioning | Implements the functionalities encapsulating the trust services functionalities.
A ‘trust service’ means an electronic service which consists of these functionalities: i) the creation, verification, and validation of electronic signatures, electronic seals or electronic time stamps, electronic registered delivery services and certificates related to those services, or ii) the creation, verification and validation of certificates for website authentication; or iii) the preservation of electronic signatures, seals or certificates related to those services. |
IM, USI, VC, S&N, LKP |
| Identity Management | Implements the functionality of user authentication.
‘Electronic identification’ means the process of using person identification data in electronic form uniquely representing either a natural or legal person, or a natural person representing a legal person; ‘Authentication’ means an electronic process that enables the electronic identification of a natural or legal person, or the origin and integrity of data in electronic form to be confirmed. |
IM, USI, VC, |
| Record Matching | Application component that provides identity matching based on attributes. Provided attributes are matched against attributes in some local registry. | IM, USI, VC |
| Data Encryption/Decryption | Application component providing encryption and decryption functionality (symmetrical, asymmetrical or a combination thereof). | IM, USI, S&N, LKP |
| Distributed Ledger | Application component that handles connections and operations related to the distributed ledger. | VC |
| Distributed Ledger Access Management | Application component that manages the access management related to Write/Read access into distributed ledger storage. | VC |
| Ledger to Agent | Interface that will connect to the Distributed Ledger (i.e., EBSI) in order to use e.g., the DID registry, Trusted Issuer Registry (TIR), Revocation list, etc. | VC |